|
 What is Code Signing / Digital Signature / Digital Certificate? (Q&A)In this Q&A page you will find answers to some common questions about code signing, digital signature, digital certificate, Microsoft Authenticode, and related. What is code signing? Code signing is the process of digitally signing software (for example a program, a component, or a driver) to confirm the author of the software and to guarantee that the code has not been changed or corrupted since it was signed. A cryptographic hash is used to ensure this. Code signing is a very effective method against malware / viruses because the operating system will immediately detected if a code signed file has been changed in any way after it was code signed. Code signing also increases the userīs trust of a software, especially for software that is downloaded from the Internet. There are large risks of launching a program that has been downloaded from the Internet it if is not digitally signed. Somebody else than the original programmer can have modified the code, and the system can not detect this. What is a digital signature? A digital signature is an electronic signature that is used to authenticate the identity of the individual or organization that signed a file (for example a program, a document, etc). The digital signature will also make sure that the original content of the file has not been changed. What is a digital certificate?  A digital certificate is an
electronic credential that verifies an individual's or an organization's
identity on the web. The identity of the digital certificate owner is
linked to electronic keys that is used to encrypt and sign digital
information. This assures that the keys actually belong to a specified
person or organization. A digital certificate has usually an expiration
date and you have to renew the certificate if it has expired. A digital certificate is an
electronic credential that verifies an individual's or an organization's
identity on the web. The identity of the digital certificate owner is
linked to electronic keys that is used to encrypt and sign digital
information. This assures that the keys actually belong to a specified
person or organization. A digital certificate has usually an expiration
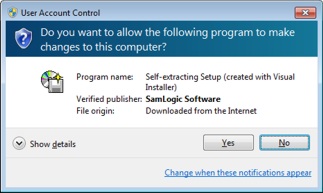
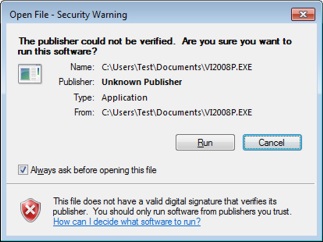
date and you have to renew the certificate if it has expired.What is a Certificate Authority (CA)? A Certificate Authority (CA) is a trusted third party organization or company that authenticates, issues and manages digital certificates. The roll of CA is to guarantee that an individual or company that have obtained a digital certificate is who he/she or the company claims to be. VeriSign, Thawte, Geotrust, Comodo and GlobalSign are examples of CA authorites. You usually have to pay an annual fee to use the services of a certificate authority. What is a Secure Hash Algorithm (SHA)? You may have seen the acronym SHA before. SHA is an abbreviation for Secure Hash Algorithm and it is an algorithm that produces hash values. A hash value is a kind of checksum value that is used to assure that data or a binary file has not been changed since creation. The computed hash value is distributed with the data or binary file, and if any portion of the data or binary file has been changed after creation, the distributed hash value will not match the next calculation of the hash value. And then we know that the data or binary file is not the original one. What is the difference between SHA-1 and SHA-2? SHA-1 and SHA-2 is a set of cryptographic hash functions designed by NSA, and is often used when code signing software. You can read this blog post on our website to get a more detailed explanation of SHA-1 and SHA-2 and read about the difference between them. What is Extended Validation (EV) Code Signing? Extended Validation (EV) Code Signing (or just EV Code Signing) is a new kind of code signing that offers higher security. Although the traditional way of code signing is quite secure, there is always a risk that code certificates are stolen by "hackers". If a code certificate is stolen then also malware from an unknown source can be code signed and fool the operating system. The famous Stuxnet computer worm is an example of a malware that worked in this way. EV Code Signing uses a hardware token and a PIN code, which will increase the security level. The digital certificate’s private key is stored on the hardware, so even if a hacker comes in the system he/she can not access the private keys. Without the private keys the hacker can not code sign any software. A more rigorous identity verification and authentication process is also used to make sure that the software developer / company can be trusted. You can read more in the EV Code Signing article on our site. What is Microsoft Authenticode? Microsoft Authenticode is a code signing technology from Microsoft. It allows developers to include digital signatures in their software, for example in Windows applications (EXE), ActiveX components (OCX), dynamic link libraries (DLL), etc. Both 32 bit and 64 bit files are supported. Microsoft Authenticode is based on an industry standard and is probably the most used code signing system today. I am a software developer, why should I code sign my software? That's for many reasons. One reason is for the increased security. A code signed software is very difficult to modify or get infected by a virus without that the operating system discovers it. If somebody try to start a modified program file, the OS will refuse to start the program. Another reason is that a code signed software will probably not give any deterrent warning message in the operating system. This will lead to that more people actually will run the program. In the two images below we show how different the messages can be dependent on if the program file is code signed or not. In the example below a setup program that has been downloaded from Internet is started. In both cases a message box is shown, but the message box that is showed for the setup program that is not code signed is harsher:
What code signing tools are available, and where to find? There are a few code signing tools included in Microsoft Windows SDK and Microsoft .NET Framework, for example the Sign Tool program. They are usually installed with the other files and you can use them when you handle digital certificates and code sign your files. A list of more tools from Microsoft is available on this page on MSDN online. We recommend you also to read the Code Signing for Developers article on Tech-Pro.net. It is very informative and shows also in detail how to code sign a software. Many setup tools have also built-in functions to code sign a created setup package. In our setup tool Visual Installer the Microsoft Authenticode technology is used to code sign installation packages. If you want to know how to code sign a setup package using Visual Installer, read the How to code sign a setup package tip page. How can I see that a file is code signed? If you want to know if a particular file is code signed you can examine this in an easy way via Windows Explorer / File Explorer. In Windows Explorer / File Explorer, right-click on the file and choose the Properties menu item. A Properties dialog box is opened, and in this dialog box, click on the Digital Signatures tab. The dialog box / the tab will look like: 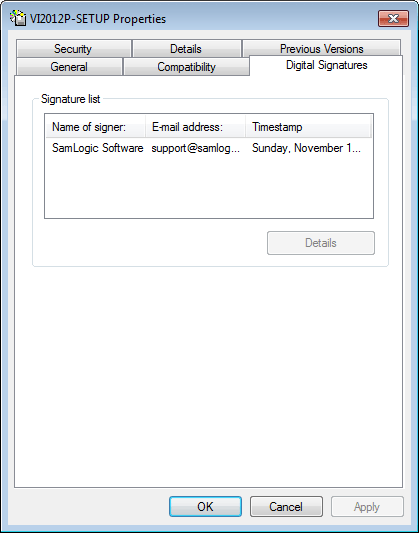 If you select the name of the signer in the Signature list list in the dialog box, the following dialog box is shown: 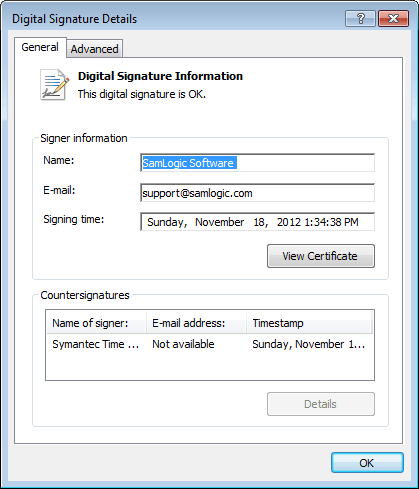 There you will find some details about the company that created the software, and details about the digital certificate.
Other articles More articles are available from the article index page. |
|
| Article written by: Mika Larramo |